I have been testing the new Cisco ISR 1113 Router from Cisco, and done a bit of a video overview. Perfect for offices and it can handle your 1Gig WAN Ethernet/SFP/VDSL/GFAST link, LTE, or even BGP,MPLS, etc and has various licensing on offer. It is also SD-WAN Ready.
Category: Cisco
I wanted to try do something on my Cisco ASA to setup incoming IKEV/IPsec/L2TP VPN to allow access to the local LAN and also the internet connection which the ASA Uses. So when a client connects to the VPN, they can access the local lan, as well as the internet connection that sits off from the ASA.
In order to set this up, we have to have something like this going, all performed in enable configuration mode.
- Define your VPN Pool of addresses eg
ip local pool VPNUsers 192.168.20.1-192.168.20.30 mask 255.255.255.224 - Relax the security rules between the interfaces a bit
same-security-traffic permit intra-interface - Create an object for example like VPN, then NAT the outside interface to the outside, this allows routing of internet from VPN to the ASA using the ASA’s ISP connection on outside
object network VPN subnet 192.168.20.0 255.255.255.224 nat (outside,outside) dynamic interface
- Allow VPN Interface “Hairpin” on same interface and access to local LAN/Internet resources
nat (outside,inside) source static VPN VPN - Create a VPN Clients Out ACL, to allow the VPN Client subnet, access from its subnet to any IP address on the outside (in our case the local LANs or internet)
access-list VPN_CLIENTS_OUT extended permit ip object VPN any - Modify the group policy tunnel attributes attached to your tunnel. In my scenario below VPN Clients will use the Cloudflare DNS, utilise the correct ACL for access, allowed IKEV or L2TP protocols, all traffic will be tunneled and no split traffic permitted on client, and the IP address pool will be utilised from our VPNUsers pool
group-policy yourtunnel attributes dns-server value 1.1.1.1 vpn-filter value VPN_CLIENTS_OUT vpn-tunnel-protocol ikev1 l2tp-ipsec split-tunnel-policy tunnelall address-pools value VPNUsers
- Once the above is implemented, the VPN clients will have access to the Local LAN, and to the Internet connected to the ASA. The above configuration does not take into consideration the complete VPN Tunnel setup, this additional configuration assumes you already have an existing complete tunnel setup.
This took me some time to get working, so I wanted to put some of my research on my blog incase anyone wishes to do the same, feedback welcome 🙂
I recently have purchased 2 x Cisco 3802 , and 2 x Cisco 1852 Access points to work with the Cisco 2504 WLC Controller. I really wanted to upgrade to AC wifi and take advantage of all that Cisco have to offer in the wireless world and put it through some tests and performance. Initially i found it great on Windows Laptops and Macbooks, however i had major issues with Apple IOS 11 and Apple TV. Connections would constantly drop and would not work as well. I was testing on the 5Ghz/80Mhz band, and i seriously thought there was an issue with this band, as switching things to 2.4Ghz/20Mhz seemed to work better.
I raised a Cisco TAC case to further investigate these issues and we found that:
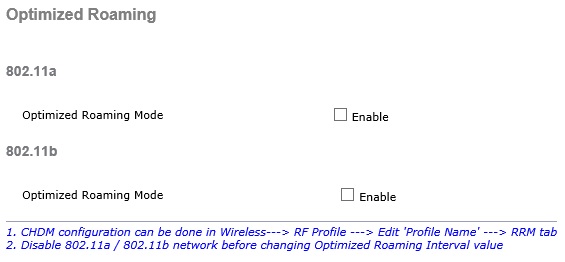
1) Optimized Roaming was enabled for 802.11a and 802.11b. (On WLC: Wireless > Advanced > Optimized Roaming)
This caused many issues with the Apple TV and Iphones/Ipads, and disabling this fixed the Apple TV, but not fully the Iphones and Ipads.
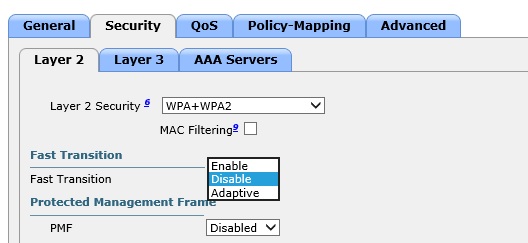
2) Fast Transition was enabled with Adaptive (On WLC: WLANS > “Your SSID” ID > Security > Layer 2 > Fast Transition)
Having Fast Transition enabled caused the significant issues with Iphones and Ipads with wireless connectivity and dropping. Once this was switched off we immediately noticed the performance improvement and roaming.
Cisco advised that the IOS 11 is buggy when it comes to the implementation of Fast Transition as we went through many debugs. They advised I needed a Apple Enterprise Support contract for Apple to just look at it, which I couldnt afford, so I have left Fast Transition “off”. The enterprise contract is like $5995 USD, or $799 USD per incident, just a bit pricy!
I also asked if there was any benefits to Fast Transition being “on”, and they advised it was only beneficial if my wireless setup is 802.1X and this improves the roaming between AP’s and going through Radius etc. My scenario only had WPA2 Pre-Shared key, so i could leave the Fast Transition set to Off without any issues.
Cisco Apple best practice document found here, advises FT should be set to Adaptive and left on, however as we found IOS 11 has severe issues with their implementation of FT..
I queried Cisco whats going on here.. and why there is so many issues and differentiates from their document and their advise was:
FT will always be suggested on Apple enterprise environment. This can’t be removed from the document simply because new iOS on some devices are having buggy issues with it. This is something that need to be fixed on Apple side and Cisco has nothing to change on the code or document since we are following the IEEE standard that we expect Apple to also follow on their entire product line.
Unfortunately as shared before to engage Apple care , you need to have an “enterprise AppleCare support agreement” contract.
TAC can’t do anything from Cisco side for this case to move further unfortunately.
So for all of you reading and have Cisco Wireless setup, running IOS 11, and are noticing problems with Apple TV/Iphones/Ipads be warned what options are set on the WLC, and how it could affect the wireless experience.
For Apple reading, please look at your FT implementation with Cisco on IOS11, so its less buggy, especially on the 5Ghz bands.
Again, thanks for reading and any feedback welcome.
4 Comments